A Security Operations Center (SOC) is a centralized unit that deals with security issues on an organizational and technical level.
The SOC consolidates under one organization functions of: incident...
Jun 03, 2019
4,128
1
Threat Intelligence - It is the one word we all have heard various times recently. The subject has been under constant scrutiny for a while now, but do we understand it? Moreover, since it has been...
Feb 28, 2019
3,500
0
In a little over a decade, the World Wide Web has evolved from purely static information repositories into highly functional applications that process sensitive data and perform powerful actions with...
Jan 03, 2019
4,472
0
The threat of cyber-attacks has more than made their presence felt across different domains throughout the world. Right from virtual bank thefts to partly candid onslaughts from nation-states, the...
Dec 26, 2018
4,103
0
Threat Intelligence (TI) is no more a costly subscription to be purchased. Thanks to the open culture drive, multiple big security vendors have made their threat intelligence platform available to...
Dec 24, 2018
6,753
4
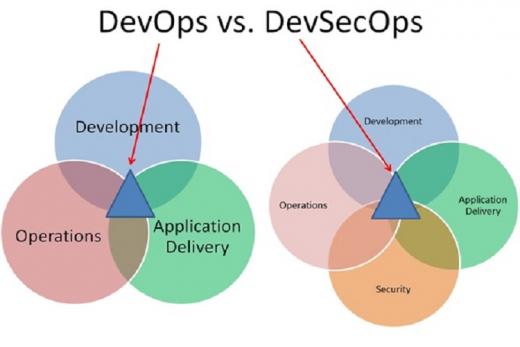
DevSecOps, or the blending of an enterprise’s applications development with systems operations teams with collaboration of security has become a trendy IT topic. The new operating model is often...
Dec 13, 2018
8,185
3
Latest security breach where hackers were able to overcome, Singapore’s much vaunted cybersecurity defenses and compromise the personal data of over a quarter of the Southeast Asian nation’s...
Nov 30, 2018
6,758
4
To keep pace with the digital economy, as enterprises race towards transforming into cloud-first businesses, the hybrid cloud environment has become commonplace. According to the Cloud Services...
Aug 22, 2018
8,897
2
Just when the global cyber community was slowly recovering from the infamous WannaCry Ransomware attacks that caused havoc across the globe last year, two recent cyberattacks of an almost identical...
Aug 02, 2018
3,629
1
It has not yet reached epic proportions, but the number of organizations adopting cloud-based technologies is growing dramatically. Organizations of all sizes across industries are turning towards...
Dec 26, 2017
3,253
0
2017 has seen a lot of cyber-attacks globally and in India. Attackers are continually evolving their tactics to evade defences, and are more regularly targeting lower-level employees who might have...
Dec 12, 2017
5,368
2
Mrutyunjay Mahapatra, Deputy Managing Director and CIO of SBI, talks about how enterprises and CIOs need to focus on security. He prescribes a framework called Step that includes security first,...
Dec 06, 2017
11,426
2
The CIO of Essar Steel says that they are prepared to tackle the latest cybersecurity threats such as WannaCry, Petya, among others.
Nov 14, 2017
5,327
0
In 2015, C level American executives saw CISOs primarily as scapegoats who should be accountable in case of a major compromise. In a survey conducted in June that year, 47% such respondents described...
Aug 25, 2017
4,133
2
Murli Menon, Director & CSO, CSR (India, Poland & Romania) and CISO, APAC, Atos talks to CSO Forum on Next Gen CSOs.
Excerpts from the interview:
How has the threat spectrum evolved in India...
Jul 25, 2017
4,931
0
Q. Can you tell us about F-Secure?
JR: F-Secure is a 20-year old company that specializes in cyber security and protecting against threats on the Internet. It has grown from a small Finnish company...
May 10, 2017
111,387
2
In the last few years, the cyber security landscape has undergone a huge transformation. Cyber criminals and hackers spare no one, and do not discriminate between enterprises and governments....
Apr 07, 2017
4,600
1
Once upon a time, not long ago—just 10-15 years to be precise—the job of an information security professional in an enterprise was to ensure that the IT systems are protected. IT systems were a...
Apr 03, 2017
3,930
0
No one forgets a breach.
In October 2016, what is being touted as the 'biggest ever breach of financial data in India', as many as 3.2 million debit cards were compromised. Of the cards breaches,...
Feb 11, 2017
10,104
0
How do you see the threat landscape evolving in 2015?
The biggest challenge is knowledge management. There is a huge shortage of skilled labour who can understand the concept of cyber security. The...
Dec 19, 2014
8,248
4
Information security has always been challenging. How do you see the threat landscape evolving in 2015?
Today organisations are moving towards BYOD and cloud architecture. It includes various...
Dec 19, 2014
3,868
0
How can you measure the current risk level as far as cyber-threats are concerned in process industries?The security of automation solutions and networks has become a critical component of plant...
Aug 25, 2014
4,804
1
Broadly, traditional CRM systems have focused on aligning organisational processes around the customer. While it remains very relevant in today’s context, changing customers’ behaviour patterns,...
Jul 17, 2014
6,037
1
Innovation has always been one of the keys to success for a CIO; and over the years, every enterprise technology decision maker has realised that the job is much more than just managing IT in the...
Jul 14, 2014
3,722
0
Technology decision makers in enterprises are often at a loss when it comes to quantifying strong business benefits accruing from their roles. They are unable to strongly position and portray...
Jul 03, 2014
3,765
0
The position of a Chief Security Officer (CSO) in an enterprise has traditionally been looked upon as a back-end role. Perceiving them as business enablers was always a far-fetched scenario. As...
Jun 27, 2014
3,891
0
The frequency of large attacks has been increasing. The common reason for these attacks is third party lapses. Vishal Salvi, Senior VP and CISO, HDFC Bank, feels it is time enterprise information...
Jun 24, 2014
3,655
0
Target Corporation has announced the appointment of Brad Maiorino as senior vice president and chief information security officer.
Maiorino will be responsible for Target’s information security and...
Jun 13, 2014
3,717
0
What if your security was breached? The question is not about “If” anymore, really. It’s only about “When” and “How”....
Recently, the information security industry was abuzz with yet another data...
Jun 12, 2014
3,546
0
What in your view is being a leader all about?
Leadership is all about people. Leaders are those who attempt to influence others' behaiviour. Leadership means achievement and the bottomline is to...
Jun 02, 2014
5,933
4
Verizon security researchers, using advanced analytical techniques, have found that 92 percent of the 100,000 security incidents analyzed over the past ten years can be traced to nine basic attack...
Jun 02, 2014
3,189
0