The world has been going through significant changes: facing a global COVID-19 pandemic, researching how the SARS-CoV-2 virus works and then delivering a defense via vaccines to fight back. Similarly, in the world of cybersecurity, we saw many changes in the first half of 2021. While DDoS attacks kept growing in size and frequency, attackers particularly focused on low-volume attacks that ran for longer periods of time, frequently injecting attack traffic. These low-volume attacks helped them evade basic defensive measures, but low thresholds still had a significant impact systems and operations, as stated by the report H1 2021 DDoS Weapons, an initiative by A10 Networks.
Report also featured some positive changes, for example, a large-scale botnet takedown by an international operation across different continents. Organizations began paying a lot more attention to DDoS, raising awareness around the role of malware in DDoS attacks, and providing insights into how systems and operations can be protected from attacks, large or small.
Finally, organizations are paying more attention to infectious malware, like Mozi, the subject of the spotlight section. In fact, some vigilante groups have even started using DDoS attacks as a defensive measure, attacking systems that exhibit scanning behavior. While employing DDoS attacks against the very attackers might be considered controversial, it helps ultimately reduce DDoS attacks and the expansion of botnets.
DDoS Weapons Intelligence and Trends
The research team gathers weapons intelligence by closely monitoring attack agents under the control of botnet command and control (C2), discovering malware innovations by deploying honeypots, intercepting self-replicating botnets, and scanning the internet for exposed reflected amplification sources.
Millions of IP addresses of exploited hosts regularly used in DDoS attacks are accumulated in voluminous feeds that include millions of entries.
During the first half of 2021, there was the same rate of growth for DDoS weapons as in the previous report, i.e., +2.5 million weapons, with a total number of approximately 15 million weapons. This number includes both reflected amplification weapons as well as botnet agents readily available for exploitation by attackers.
DDoS Botnet Agents
Compute nodes like computers, servers, routers, cameras, and other IoT devices infected by malware and under the control of a malicious actor are the prized tools for motivated DDoS attackers. These weapons, commonly referred to as drones, bots or botnets, can easily be sourced from different locations, depending on the attacker’s requirements.
Each report also provides an in-depth look into high-activity hubs in order to help organizations protect their systems and resources from potential DDoS attacks sourced from these botnets.
Top ASNs Hosting DDoS Weapons
This section of the report has proven to be the most dynamic we observed with organizations rising and falling in prominence during every reporting period, primarily because of the distributed nature of DDoS attacks and the weapons they use.
Hathway India showed a spike in botnet activity during the second half of 2020, making up 26 per cent of the total number of global botnets. These systems went offline soon after they were discovered. This was either entirely or in part a result of a vigilante group claiming to have taken these systems down. In contrast, Hathway India made up only 3 per cent of the total number of bots in H1 2021. At the same time, China Unicom rose to the top of the list, hosting 23 per cent.
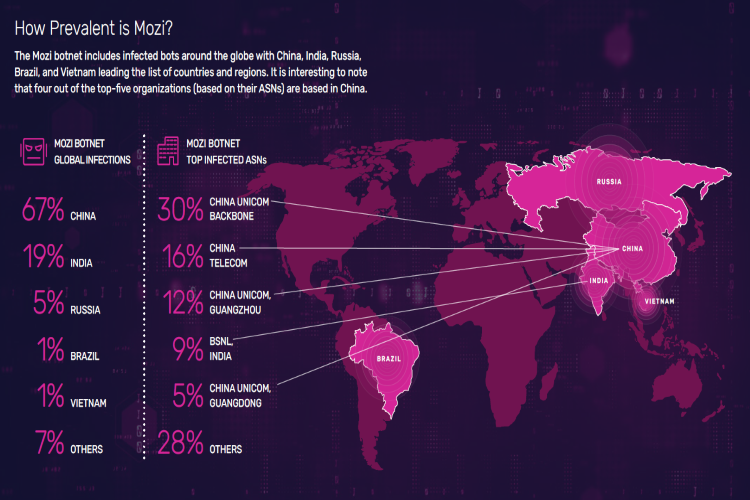
What is Mozi?
Mozi is a DDoS-focused botnet that utilizes a large set of Remote Code Executions (RCEs) to leverage CVEs in IoT devices for infection. These IoT devices include readily available and commonly used DVRs and network gateways. Once infected, the botnet uses peer-to-peer connectivity to send and receive configuration updates and attack commands.
Mozi was first identified in 2019 and has been evolving and increasing in size ever since. It can now persist on network devices by infiltrating the device’s file system, remaining functional even after the device has been rebooted.During the first half of 2021, Mozi topped out at over 360,000 unique systems using more than 285,000 unique source IP addresses, likely due to address translation.
Are Amplification Attacks Still Used?
Lately, DDoS attackers have been increasingly focused on smaller attacks launched persistently over a long period of time. The trend has been prevalent throughout the last couple of years thanks to the COVID-19 pandemic. That said, the notoriety and capabilities of large-scale DDoS attacks cannot be diminished.
In fact, while large-scale attacks might not occur as frequently as their low-volume, high-frequency cousins, they still tend to cause a lot of damage and make headlines at least a couple of times a year. At the end of the day, while these large-scale attacks might not be as lucrative as continuously attacking an organization for days or even weeks, these attacks are increasingly used to make a statement. And in a world where state-sponsored cyberattacks and cyberactivism have quickly become a norm, these attacks can be quite damaging.
DDoS Weapons and Threat Intelligence
Sophisticated DDoS threat intelligence, combined with real-time threat detection, artificial intelligence (AI)/machine learning (ML) capabilities, and automated signature extraction, allow organizations to defend against all kinds of DDoS attacks, ranging from low-volume, high-frequency persistent attacks to massive multi-vector DDoS attacks, no matter where they originate.

 In
In
Add new comment