
Mobile/IoT devices are increasing day-by-day and digital payment industry is also on the peak. IoT and mobile devices has a great impact on human lives, it is penetrating numerous aspects in human lives by obtrusively working in the background without making realizing its presence for us. IoT devices are everywhere near us these days which includes smart cars, drones, health monitors, doors, windows, fans, TVs, refrigerators and electronics appliances in a smart home, smartwatches, etc. All these IoT based devices can easily be operated with the help of mobile applications. Most of digital payment apps, messaging apps are also on mobile devices or IoT devices. With the growing popularity of Mobile and IoT technology and increased demand for connected devices, cyber criminals are also increasing day-by-day and current authentication and infrastructure is not much capable to track cyber criminals.
So what’s next in Payment industry to track and reduce Cyber Crime?
- Biometric Authentication to reduce Cyber Crime: Considering the spectrum of law enforcement, biometric authentication can play a key role to stop and track cyber criminals. This solution enables law enforcement agencies to identify cyber criminals through their physical or behavioral characteristical biometric data. Moreover, fingerprint sensors, face recognition, Iris scan are also significantly emerging as the latest trends in providing civil identity, voter registration and population registration.
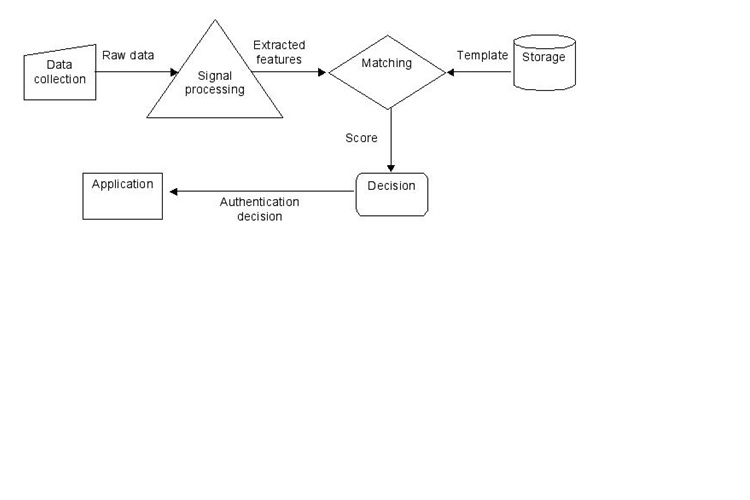
- Aadhaar/ Biometric Authentication in Indian Payment Infra: Aadhaar Authentication provides a digital, online identity platform so that the identity of Aadhaar number holders can be validated instantly anywhere at any point of time. Aadhaar-based authentication as a service can be utilized by the requesting entities to authenticate the identity of the users based on the match of their personal identity information before providing them access to their services or business functions. Providing services through information technology infrastructure creates a great impact in organizations. To expand the reach of these organizations, verifying an individual’s identity fulfils an important aspect of security.
Who should move to this Solution and help nation to reduce Cyber Crime?
Finance companies, Mobile Payment Apps, Public & Private sector Banks and all Digital Payment industry should start moving in the direction of biometric authentication as a 2nd level authentication mechanism. Authentication remains one of security’s biggest concern in today’s fast growing scale of Cyber Crimes. Using multiple factors in authentication mechanism, makes the authentication more stronger and reliable by adding additional layers of security.
Techniques to Control Cyber Frauds: An example of Next-Gen E-Wallet to E-Wallet transaction:
Biometric authentication can play an important role in reduction of cyber crime and can control E-wallet and digital transaction frauds to a greater extent. In this biometric authentication mechanism, the sending party and receiving party will use biometric authentication in their process of digital transaction. This transaction process will help the concerned authority to track or record digital money, which in return will be helpful to catch cyber frauds. Hence, reducing the statistics of cyber frauds involved in these E-wallet and digital transaction process to a significantly greater extent.
Let us understand: The workflow and concerned postulates involved in the biometric authentication mechanism in this digital transaction process considering Paytm as an E-Wallet.
Step 1: Paytm User A (Sending party) will be transferring digital money to Paytm User B (Receiving party).
Step 2: 1st authentication process involved for User A is the PIN and the 2nd authentication process is his biometric authentication from the Aadhaar.
Step 3: The Receiving party, User B will have the PIN as his 1st authentication process and the biometric authentication as the 2nd authentication process to verify funds.
Step 4: Now, the User B will virtually receive the money transferred from User A, with his PIN. But, in order to use the money, User B will have to process biometric authentication through Aadhaar linked with his account.
Time-Based Multi-Factor Authentication:
This approach uses a secret shared between the server and the client (typically a mobile app) in conjunction with the current time to generate a one-time use code. The client knows the code by running the shared secret through the algorithm. The server can verify the posted code by running the same secret through the algorithm. The code is only valid for a set amount of time, usually 30 seconds.
The flow looks like this:
- You log into an application with your username and password.
- You see a text field, asking you to input the latest code.
- You launch your TOTP client on your mobile phone and see the current code.
- You enter the code in the text field and proceed on to the application.
It’s more secure than the SMS approach, because there is no medium of transmission for the code. It is generated by the algorithm. The shared secret must be kept a secret for this approach to remain secure.
One of the most popular implementations is the Google Authenticator. It makes the TOTP approach easier to use by showing the secret as a QR code that most mobile apps can read. This is much more reliable and easier to use than the manual input of a shared secret.
Benefits Involved and Need of Hour in Country to make Payment Infra Secure
- Receiving party and sending party is under biometric surveillance and Govt, Police and national forces can track any cyber crime, which is happening through banks/wallets and E-banking.
- Reduction in Cyber Crime and easier tracking of Cyber criminals and frauds.
- Need of hour to prevent financial infra/consumers with next gen level authentication solution.
- Digital Money transaction tracking or record becomes simpler, flexible and reliable.
- Tax benefits to govt involved in these digital transaction process.
- 99% reduction in Cyber Crime in the Payment industry, improves security and reduces the risk of an intruder gaining access to critical financial systems and data.
- Reduction in the state of corruption to a greater extent.
Challenges Involved but Achievable:
- Potential cost increase for things like additional support, training, maintenance, SMS Gateway or services, hardware and software tokens.
- Infrastructure upgrade for the Mobile system, Data centers and secure backend & frontend code review for the application.
- Good Internet-connectivity and bandwidth within the Country.
- Encouragement of Cyber Awareness to the Consumers through Cyber Security awareness campaign, seminars, training, etc.
The author is LLB, LLM (Cyber Laws)

 In
In 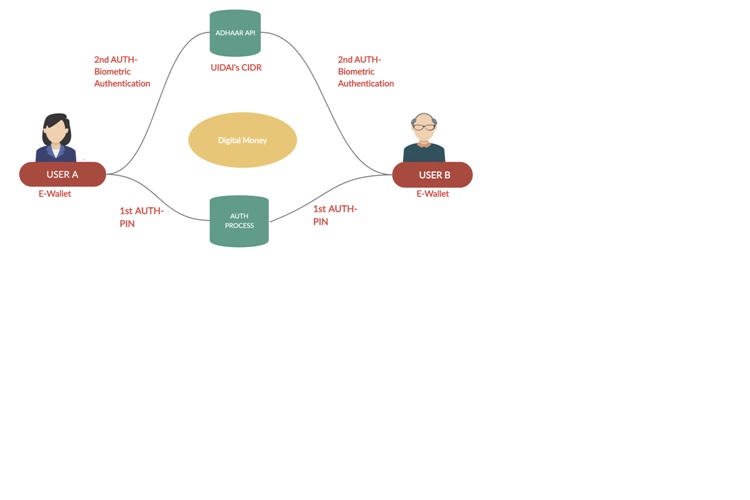
Comments
Discount Zentel With Free
Discount Zentel With Free Shipping https://buycialisuss.com/ - Buy Cialis Gnc Natural Viagra <a href=https://buycialisuss.com/#>Buy Cialis</a> Can Keflex Antibiotic Cause Nightmares
Discount Zentel With Free
Discount Zentel With Free Shipping https://buycialisuss.com/ - Buy Cialis Gnc Natural Viagra <a href=https://buycialisuss.com/#>Buy Cialis</a> Can Keflex Antibiotic Cause Nightmares
Discount Zentel With Free
Discount Zentel With Free Shipping https://buycialisuss.com/ - Buy Cialis Gnc Natural Viagra <a href=https://buycialisuss.com/#>Buy Cialis</a> Can Keflex Antibiotic Cause Nightmares
Tomar Viagra Yahoo https:/
Tomar Viagra Yahoo https://cheapcialisir.com/ - buy cialis and viagra online Keflex Pipe Expansion Loops <a href=https://cheapcialisir.com/#>Cialis</a> Levitra 10 Mgptt
Tomar Viagra Yahoo https:/
Tomar Viagra Yahoo https://cheapcialisir.com/ - buy cialis and viagra online Keflex Pipe Expansion Loops <a href=https://cheapcialisir.com/#>Cialis</a> Levitra 10 Mgptt
Tomar Viagra Yahoo https:/
Tomar Viagra Yahoo https://cheapcialisir.com/ - buy cialis and viagra online Keflex Pipe Expansion Loops <a href=https://cheapcialisir.com/#>Cialis</a> Levitra 10 Mgptt
Add new comment